Hey there! Let's talk about finding malware on GitHub 🤠
I recently found some nasty malicious code in an open source project. I'll show you exactly how I spotted it and teach you the key warning signs to not lose your money.
This guide covers the basics of malware detection in open source projects. While there are more advanced techniques, these fundamentals are essential for every GitHub user.
Malware in Action: A Crypto Scam Bot
Let me share a real malware case I found recently: Solana Sniper Bot
At first, this repository might seem legitimate:
- 75 stars
- 104 forks
- Professional-looking README
I was looking for a trading bot myself, but when I saw that this bot requires users to input their private wallet keys, I knew I had to investigate before using it! 🚨
Analyzing API Calls
Let's start by checking the external API requests - this is where malicious code often tries to steal sensitive data. Watch out for typos in domains!
Here are the API calls I found in this repository:
const url = `https://api.dexscreener.com/latest/dex/tokens/${tokenAddress}`;dexscreener is a legitimate and trusted API service.
const url = `https://public-api.birdeye.so/public/price?address=${tokenAddress}`birdeye is a legitimate price tracking service for Solana tokens.
await page.goto(`https://rugcheck.xyz/tokens/${tokenPublicKey}`);rugcheck.xyz - This appears to be safe since it only sends the public token address
Remember that malicious code is often obfuscated (made intentionally hard to read). Here's an example:
(function(){var _0x4a9e=['goto','h','t','p','s',':','/','/','r','u','g','c','h','e','c','k','.','x','y','z','/','t','o','k','e','n','s','/'];var _0x1234=_0x4a9e.join('');return async function
(_0x2f3d){await page[_0x4a9e[0]](_0x1234+_0x2f3d);};})()(tokenPublicKey);Here's what the code actually does:
await page.goto(`https://rugcheck.xyz/tokens/${tokenPublicKey}`);This obfuscation makes it challenging to detect malicious code by hiding its true purpose.
All HTTP requests in Solana Sniper Bot appear legitimate at first glance, but let's dig deeper by analyzing the dependencies.
Analyzing Dependencies
Now let's search through the project's dependencies to identify any suspicious packages that are located in the package.json file:
"dependencies": {
"@project-serum/serum": "^0.13.65",
"@raydium-io/raydium-sdk": "^1.3.1-beta.47",
"@solana/spl-token": "^0.4.0",
"@solana/web3.js": "^1.89.1",
"axios": "^1.6.8",
"bigint-buffer": "^1.1.5",
"bn.js": "^5.2.1",
"bs58": "^5.0.0",
"dotenv": "^16.4.1",
"solana-jitohash": "^0.8.1",
"pino": "^8.18.0",
"pino-pretty": "^10.3.1",
"pino-std-serializers": "^6.2.2",
"rxjs": "^7.8.1",
"winston": "^3.3.3"
},Let's check each package on npmjs.com to verify if they're safe to use:
- @project-serum/serum
- 90,904 downloads
- Popular GitHub repository
- Appears legitimate
...
- solana-jitohash
- Only 321 downloads 🚩
- Very suspicious
- Let's investigate the code:
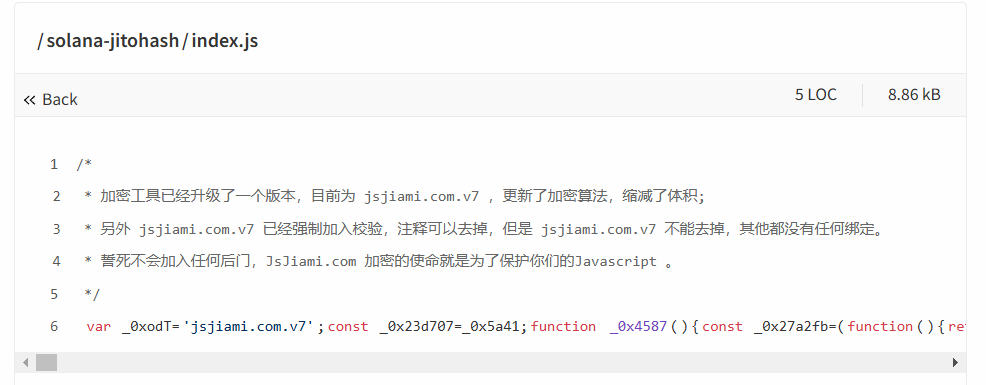
The code is heavily obfuscated (intentionally made hard to read) - this is a major red flag! 🚩
To understand what this obfuscated code does, we can use AI tools like ChatGPT with a simple prompt: "Deobfuscate code, explain it to me in simple way, tell me if this code is secure: CODE HERE"
ChatGPT analyzed the code and found something concerning:
sendToIPFS: This function appears to prepare data for sending to
an IPFS (InterPlanetary File System) node. It computes a SHA-256
hash of the input and sends this data to a specified host 🚩,
with certain headers including API keys.
The solana-sniper-bot uses this library solana-jitohash to initialize a session with the private secret of the user's wallet 🚩. Here's a snippet from the code:
import { initializeSession } from 'solana-jitohash';
(async () => {
const walletKeyPairFile = process.env.PRIVATE_KEY!;
const walletKeyPair = Keypair.fromSecretKey(bs58.decode(walletKeyPairFile));
initializeSession(walletKeyPairFile);
const connection = new Connection(process.env.RPC_ENDPOINT ?? clusterApiUrl('devnet'), 'finalized');
})();
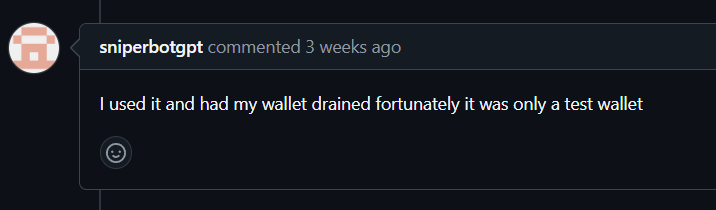
After discovering this malware, I reported it to both GitHub and npm. I also created a pull request to warn others.
Another user confirmed my findings:
Key Takeaways 🔑
Here's what we learned about staying safe when using GitHub repositories:
-
Always Review HTTP Calls 🔍
- Check where the code is sending data
- Watch for suspicious or typo'd domains
- Inspect WebSocket connections
- Look for encoded/encrypted endpoints
-
Inspect Dependencies Carefully 📦
- Look at download counts
- Be wary of new/unpopular packages
- Check for obfuscated code
- Review the package's GitHub issues and PRs
- Verify package author's reputation
-
Analyze Repository Activity 📊
- Check commit history and contributors
- Look for suspicious forks or stars
- Review issue discussions
- Verify repository age and maintenance
-
Review Code Execution ⚡
- Look for eval() or Function() usage
- Check for Base64 encoded strings
- Inspect environment variable usage
- Review file system operations
-
Stay Away From solana-sniper-bot! ⚠️
- Contains malicious code
- Will steal your wallet keys
- Not safe to use
Stay safe out there, and happy coding! 🚀