In this article, I'll break down a scam on X platform. The scams were raported publicly by some popular X influencers.
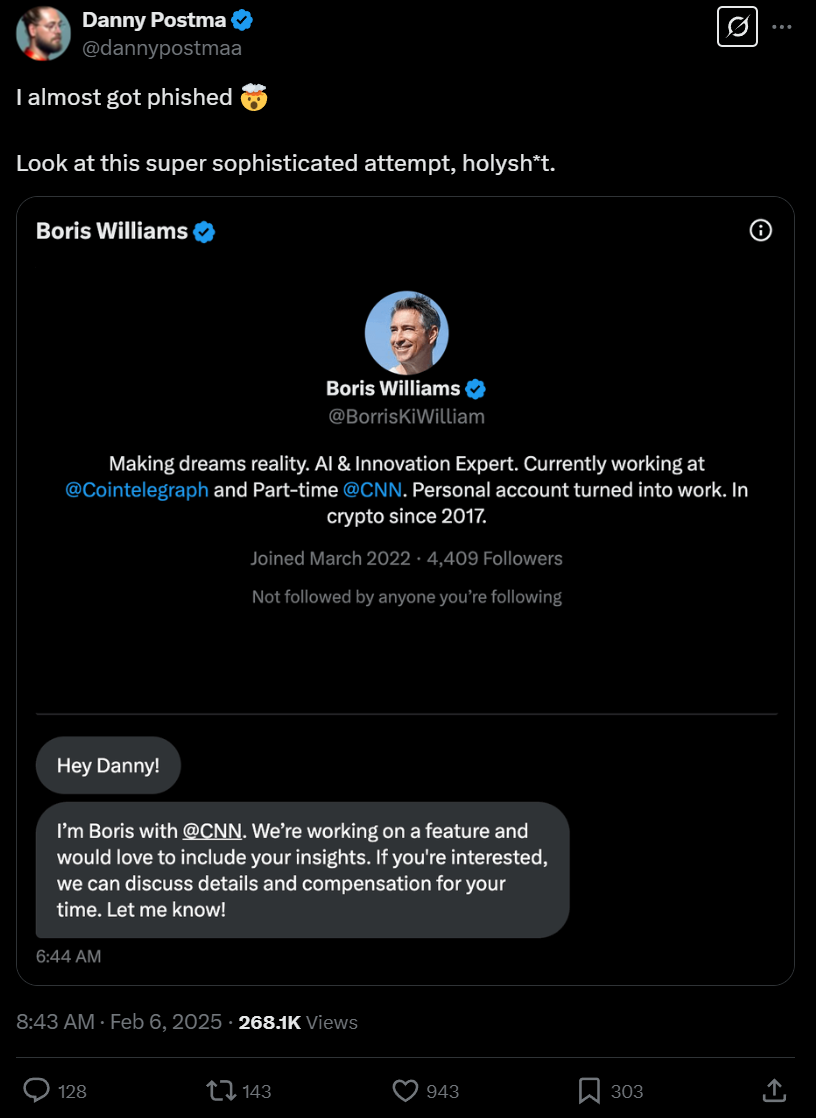
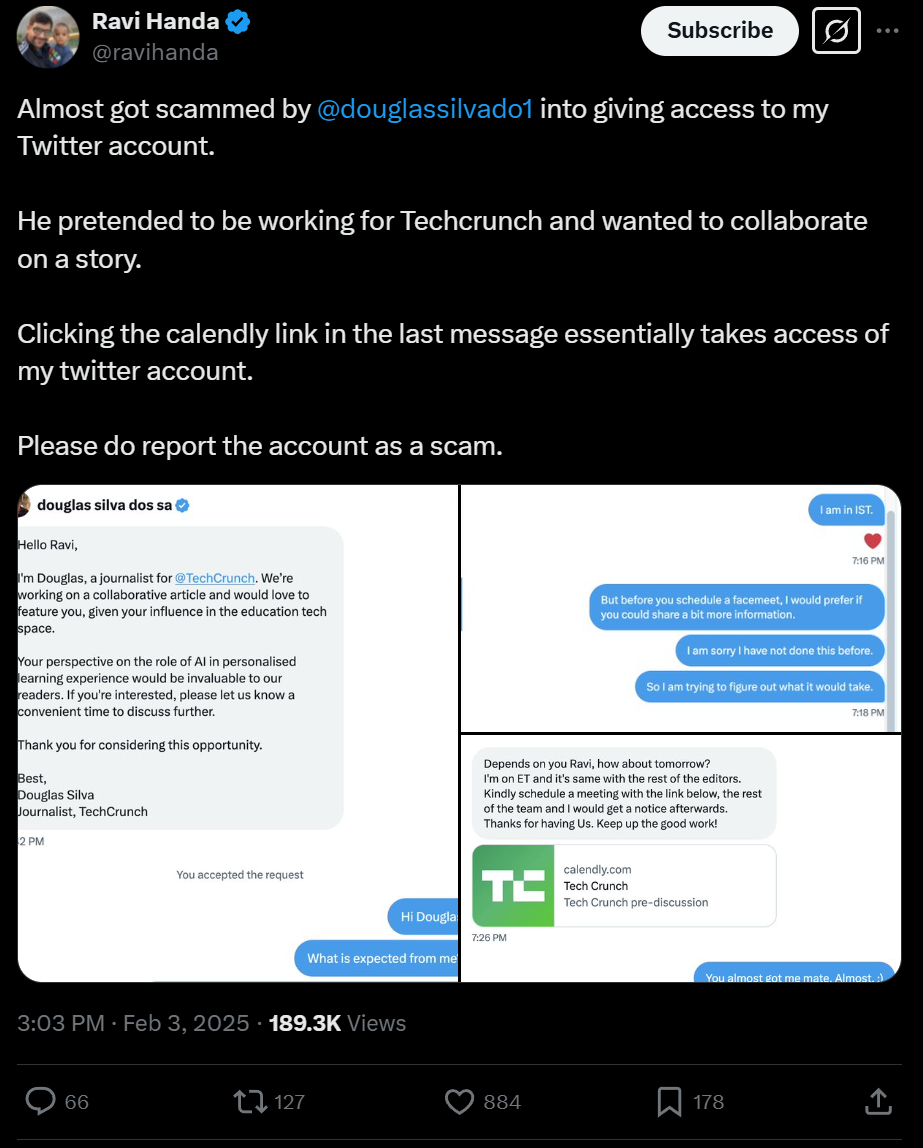
How did the hacker fake the URL on X dms?
This screenshot shows a deceptive X direct message. While the link appears to go to calendly.com, it actually redirects users to a malicious scam website.
The hacker used a simple trick to show different URLs to different visitors:
- When Twitter's preview bot visited the link, it showed calendly.com
- When real users visited, they saw a fake login page instead
This made the link look legitimate in Twitter previews while actually being malicious.
Here's how to do this URL redirect trick using Cloudflare:
Step 1: Access Cloudflare Dashboard
- Log in to your Cloudflare dashboard
- Select your domain (e.g. pulik.dev)
- Navigate to "Rules" → "Create rule"
Step 2: Create Twitter Bot Redirect Rule
Create the first redirect rule to handle Twitter bot requests:
Rule Name: Twitter Bot Redirect at /r
Match Conditions:
- URL Path equals
/r - User Agent contains "Twitterbot/1.0"
Then:
- Dynamic Redirect to
https://calendly.com - Status Code: 301 (Permanent Redirect)
Step 3: Create Default Redirect Rule
Create the second rule to handle all other requests:
Rule Name: Default /r Redirect
Match Conditions:
- URL Path equals
/r
Then:
- Dynamic Redirect to
https://google.com - Status Code: 301 (Permanent Redirect)
For cPanel users, you can achieve the same redirect behavior by adding these rules to your .htaccess file:
RewriteEngine On
RewriteCond %{HTTP_USER_AGENT} ^Twitterbot/1\.0
RewriteRule ^ https://cnn.com [R=301,L]
RewriteRule ^ https://google.com [R=301,L]
You can now test your redirect by visiting (domain).com/r
OAuth Apps Access Red Flags 🚩
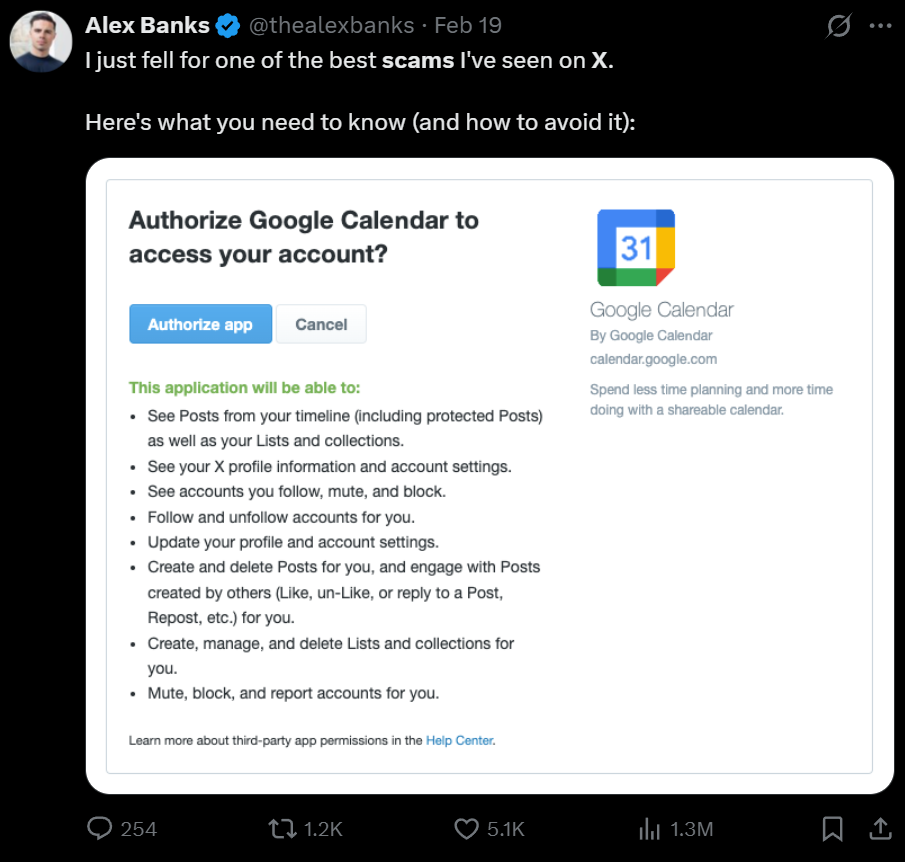
Never authorize apps that can:
- Post or delete content on your behalf 🚩
- Make profile changes 🚩
- Read your private messages 🚩
These permissions are major red flags - always decline them.
If you give an app permission to read your private messages, hackers can steal all your private conversations.
X platform allows users to specify any domain for OAuth redirects, including trusted domains like calendar.google.com. This is a security risk.
How to Protect Yourself from URL Spoofing Attacks
Having a strong password or two-factor authentication isn't enough protection. These scams can still work even with these security measures in place.
If you accidentally authorized a suspicious app:
- Go to https://x.com/settings/connected_apps
- Review all connected apps and what they can access
- Revoke any apps you don't recognize or trust
- Go to https://x.com/settings/sessions
- Log out from any unfamiliar devices
Stay safe and thanks for reading! 🔒